Four benefits of using a reverse proxy server
We recently wrote an overview to help understand proxy servers that touched on reverse proxy servers. Because reverse proxy servers are such a valuable tool in your network security arsenal, we wanted to spend a bit more time reviewing their benefits in this post.
What is a reverse proxy server?
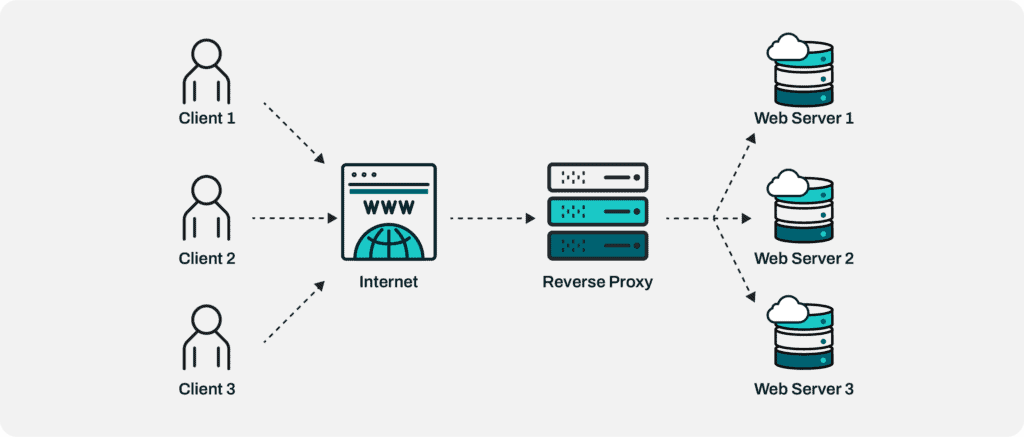
As covered in our previous post, reverse proxy servers act as an intermediary between the open internet and your network. Rather than allowing clients to directly connect to your applications and resources, the proxy fields client requests, filters and organizes them according to your policies and then distributes the requests to their internal destinations. The reverse proxy server then receives your network’s responses and sends them back to the requesting clients.
What are the main benefits of using a reverse proxy server?
Organizations implement reverse proxy servers to help in the following areas:
1. Improved security
Reverse proxy servers offer a number of security advantages over direct network connections to the web. These advantages include:
- Network anonymity: You can configure your reverse proxies so that you only expose the proxy server’s IP address to external clients. Clients generally will not be aware that they are interacting with a reverse proxy server, which improves your security by preventing a third party from capturing your network IP addresses and infrastructure.
- Reduced attack surfaces: To reduce potential attack surfaces, you can configure your internal network to only respond to requests from your proxy server. This approach does have some downside, however, as you may still need to allow for remote administrative connections.
- Data loss prevention (DLP): Reverse proxy servers can serve as a final checkpoint for DLP tools like ICAP scanning or content filtering processes before your data leaves your organization. In the event of an employee mistake, internal breach or other unauthorized access, your proxy server may still be able to prevent the transfer if you have DLP tools in place.
- Additional authentication: Configuring your proxy to request authentication may help you catch compromised credentials before the attempt reaches your internal systems.
2. Better resource management
- Speed and bandwidth optimization: Reverse proxies can be configured to handle a number of actions that improve data transfer speeds, including content compression.
- Load balancing: Proxy servers excel at distributing traffic volumes across web servers to manage high visit volumes and are the backbone of most content delivery networks.
- Encryption: For encrypted traffic, proxy servers can handle the TLS or SSL encryption process to limit the computational load on your internal network.
- Caching: In addition to caching static content, proxy servers can pre-load dynamic content to improve overall client page load speed. This content would be loaded once at the beginning of a session and then served from the proxy instead of a database call as the client progressed through the session.
3. Redundancy and failover
Reverse proxy servers can support redundancy and failover activities by being equipped with rules to re-distribute traffic in the event of an internal resource failure. They can also operate as a failover device in case of an event such as a DDoS attack. For example, if your intranet portal site is experiencing issues, your staff could use an alternate address protected by another reverse proxy server to maintain uninterrupted access.
4. Distributed architecture
Administrators supporting a distributed, cloud or hybrid client base can find reverse proxy servers helpful when trying to add additional layers of security to specific portions of the organization’s network. For example, a proxy could sit at the destination of your external VPN to perform a final authentication verification before allowing intranet access. Or, you could route any staff requests for financial information to a proxy server to perform DLP checks before completing the requests.
We hope the above information has been helpful in building your understanding of reverse proxy servers. If you have any questions about using them in your secure file transfer operations, please contact our support team.