Continuing our guide to the SSH2 File Transfer Protocol (more commonly known as SFTP), this post addresses the protocols and ports involved in SFTP so that you can easily understand how connections between SFTP servers and clients operate.
Need to Know More About SFTP?
- Differences Between SFTP and FTPS
- SFTP Concepts
- SSH and SFTP Features Supported by Cerberus FTP Server
SSH2 Protocol Use Cases
The SSH2 network protocol allows an encrypted data stream to be established between a client and a server over an unsecured network. While SSH2 can secure any network service, typical use cases include:
- Providing secure access for users
- Managing network systems and access (issuing remote commands, forwarding communications requests, etc.)
- Securing data exchanges between automated processes
- Transferring or manipulating files (via SFTP)
SFTP Protocol Connection and Authentication
The SSH2 File Transfer Protocol typically initiates a connection via the following process:
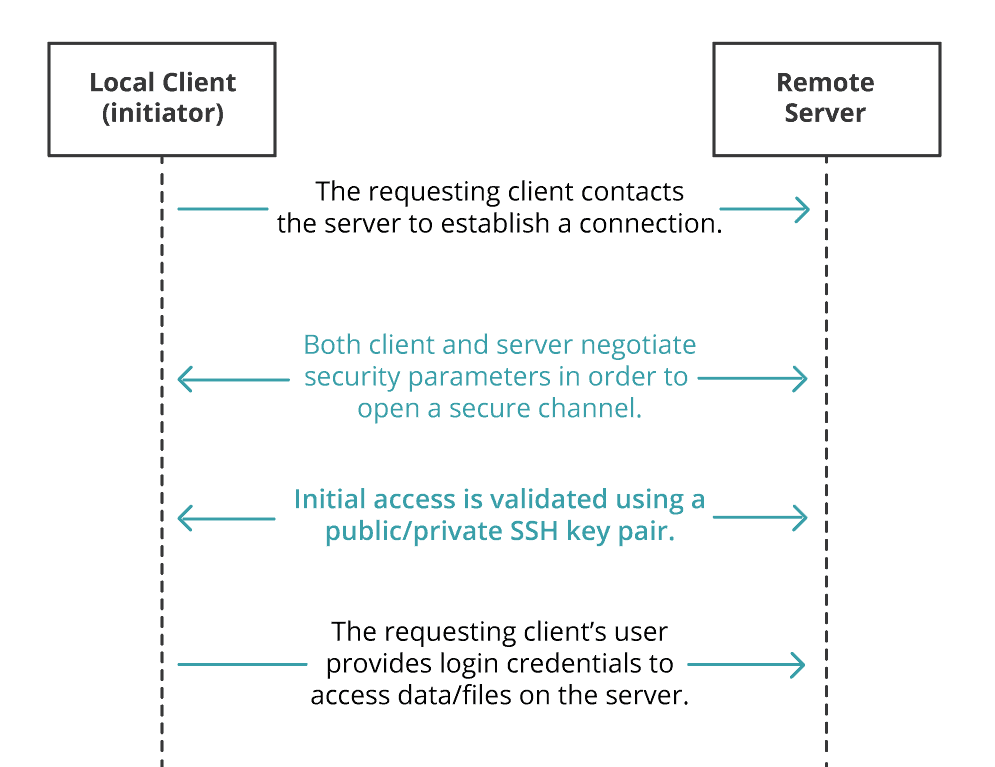
1. The requesting client contacts the server to establish a connection
SSH typically uses port 22 to establish a connection with an SFTP server. Once your firewall is configured to allow access to this port (or whichever port you specify for SFTP connections), a listener will monitor it for connection requests. Listeners are generally configured via your SSH server’s administration system.
A number of SSH servers exist, including Cerberus FTP Server. To configure an SSH2 SFTP Listener in Cerberus FTP Server, click here.
2. Both client and server negotiate security parameters in order to open a secure channel (the SSH tunnel or “secure shell”)
During this negotiation, the client and the server choose the specific symmetric encryption algorithm that will be used for the session from a set of standards available to both machines. SSH2 supports a number of ciphers and MAC algorithms for this purpose.
Once the initial connection is encrypted, the client and server then establish the encryption protocol that will be used to transmit data and validate each other’s identity through a key exchange. The most common are Diffie-Hellman and elliptic curve Diffie Hellman (see the full list of SSH2 Key Exchange Methods, Ciphers and MAC Algorithms Cerberus supports here).
3. The requesting client’s user provides login credentials to access data/files on the server
This step represents the final user-facing access check, and may not always be required (although doing so is recommended). Administrators have two options for client authentication: passwords and SSH keys, and SFTP servers typically allow both to be used concurrently. Depending on a network’s security configuration, a client may only need to provide its credentials on first connection.
More on SFTP Key Management
SFTP/SSH Key Generation
SSH keys are generated in public/private pairs, with the public key used during initial transmission to authorize a session but the private key remaining secret to validate the key pair itself. Both the client and server will exchange public keys and await a response that proves that the other party is who it claims to be (using a decrypted response via the private key) before proceeding to the main session.
Key pairs can be generated and stored on the client or server machine, with the primary security concern being keeping the private key secure. Cerberus FTP recommends generating the SSH key pair on the client machine to minimize this risk.
Keys can be generated automatically at the time of connection, or manually, and can be used in conjunction with other security/identity authentication processes. Typical practice is to assign each public key to a specific user in order to track network access.
SFTP/SSH Key Security Management
One of the most common security concerns with the SFTP protocol is SSH key management. Administrators may experience challenges with private key distribution as well as self-provisioned or abandoned keys. As SSH keys by themselves do not validate a user’s identity, it is important to ensure that keys are monitored and managed on a regular basis.
Unlock the full potential of SFTP keys in securing your file transfers. JSCAPE, also part of the trusted Redwood Software family, delves into the nuances of SFTP key management and two-factor authentication on the blog: ‘What Is An SFTP Key?‘